What is privileged access?
Privileged access refers to the level of access or permissions granted to a user or entity within a system or organisation.
This level of access is typically reserved for individuals or entities who require access to sensitive data or systems, such as network administrators or IT staff.
Privileged access often includes the ability to perform administrative tasks, make changes to system configurations, and access confidential information.
If an unauthorized user gains privileged access, they may be able to exploit vulnerabilities, steal sensitive data, or cause significant damage to systems and infrastructure. As a result, it is important for organisations to carefully manage and monitor privileged access to reduce the risk of security breaches.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
What is privileged access management?
The practice of controlling and monitoring the use of privileged access.
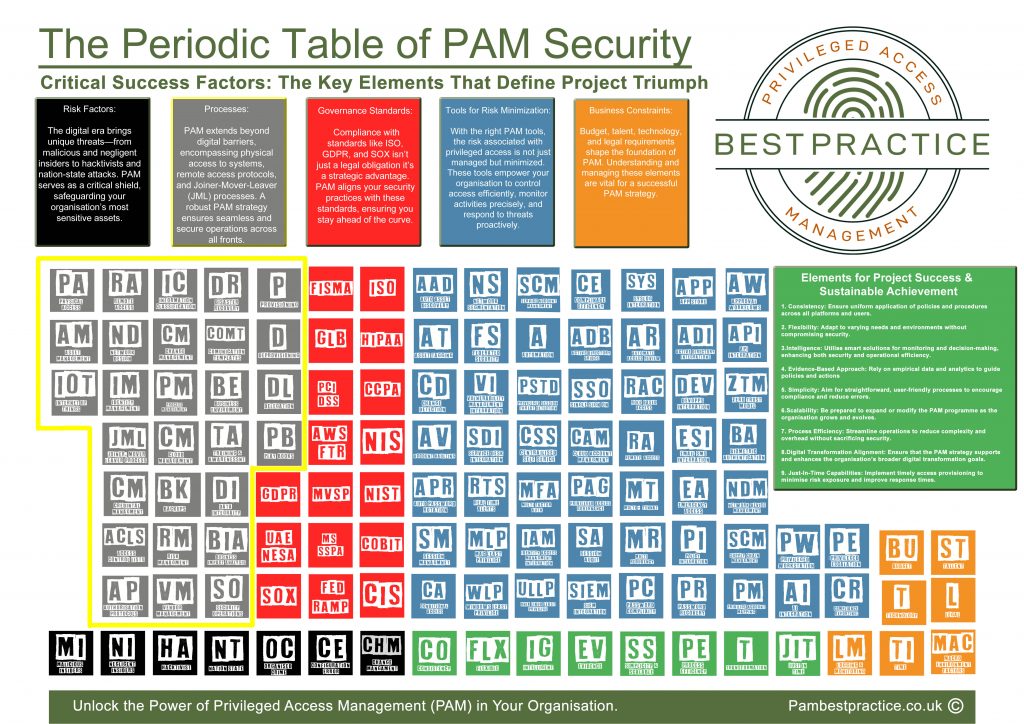
We are excited to introduce the innovative Privileged Access Management Periodic Table, a unique tool designed to encapsulate every element that impacts a PAM project. This comprehensive framework ensures an holistic approach to your PAM initiatives, making certain that no critical aspect is overlooked.
Our course is meticulously structured around this periodic table, focusing on each element to provide you with a thorough understanding of all factors influencing successful PAM implementation.
Whether you are starting a new project or refining an existing one, our training will equip you with the insights and tools needed to manage and secure privileged access effectively.
Join us to explore the depths of PAM and ensure your projects are comprehensive and secure.