Guarding the Digital Gates: The Critical Role and Dynamic Journey of Privileged Access Management in Cybersecurity.
The domain of Privileged Access Management (PAM) stands at the forefront of cybersecurity, where it acts as the custodian of the keys to an organisation's most critical and sensitive systems.
At its heart, PAM is not just about technology; it's about safeguarding the very backbone of our digital infrastructure against a vast and evolving threat landscape.
This field promises an exhilarating journey for those intrigued by the complexities of cybersecurity and eager to make a tangible impact in protecting against dire threats.
In the ever-changing digital world, the risks to our most sensitive data and systems come from a variety of malevolent actors, each with their unique motivations and methods. Negligent insiders, often overlooked, can cause as much damage as external threats through mere oversight or lack of awareness, underscoring the need for robust PAM strategies that go beyond technology to encompass comprehensive user education and behavioral analytics.
Hacktivists and nation-state actors present more sophisticated challenges, employing advanced techniques to bypass traditional security measures in pursuit of political, ideological, or strategic gains. Their targeted attacks on privileged accounts demonstrate the critical importance of securing these access points to protect national security interests and corporate intellectual property.
Organized crime syndicates, driven by the lure of financial gain, exploit any vulnerability in the armor of organizations, making the role of PAM in financial sectors and beyond not just a matter of compliance, but a crucial pillar of defense against fraud and theft.
The pitfalls of configuration errors and poor change management represent another significant risk, often turning the very systems designed to protect us into liabilities. These operational challenges highlight the need for meticulous attention to detail in PAM processes and the implementation of robust oversight mechanisms to ensure that the protective measures we rely on do not become our Achilles' heel.
Embarking on a career in the PAM space is not just about understanding the nuts and bolts of technology; it's about delving into the psychology of attackers, anticipating their moves, and staying one step ahead. It requires a blend of technical acumen, strategic thinking, and a deep commitment to safeguarding our digital future.
For those drawn to the challenges and complexities of cybersecurity, working in PAM offers a unique opportunity to be at the heart of the action, where the decisions you make can have a profound impact on the security posture of organizations and, by extension, the safety of the digital world at large. The journey into the realm of Privileged Access Management is not just a career path; it's a calling for those dedicated to making a difference in the ever-evolving battleground of cybersecurity.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
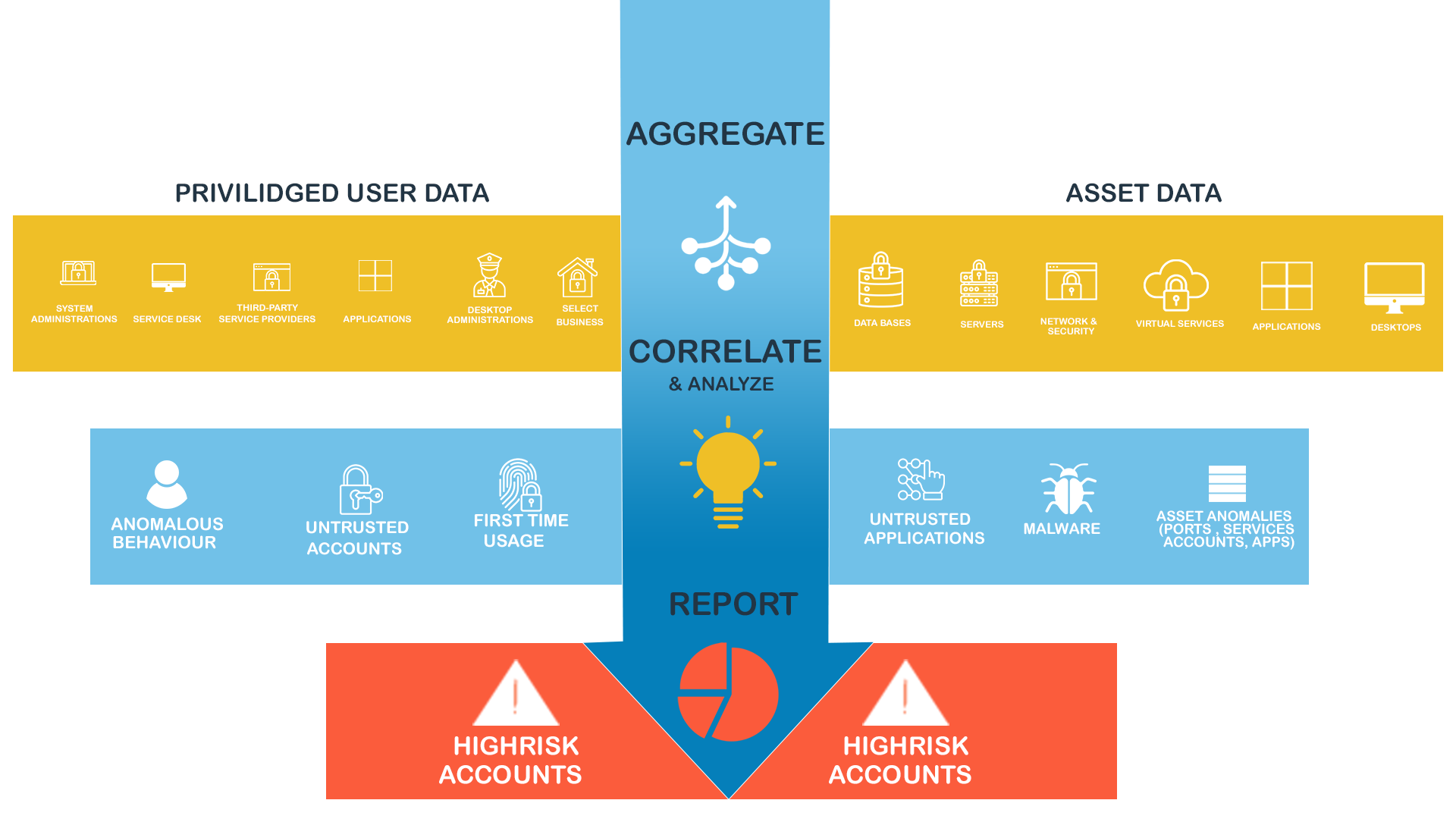
What is privileged access management?
The practice of controlling and monitoring the use of privileged access.
Privileged access management (PAM) is the practice of controlling and monitoring the use of privileged access (i.e., administrative or superuser access) within an organisation.
This typically involves the use of security measures and controls to ensure that only authorized users are granted access to privileged accounts and functions, and that the use of such privileges is monitored and audited.
Privileged access management is important because it helps to protect against unauthorised access to sensitive systems and data, and to ensure that only authorised users are able to perform certain actions that could have a significant impact on the organization.
Some common components of Privileged access management include privileged account password management, least privilege principles, access control, and auditing and reporting.