Master Advanced Privileged Access Management: Protect Your IT Infrastructure with Our Specialized Course
Step into advanced Privileged Access Management (PAM) with our course designed to equip you with strategies to protect your IT infrastructure. Master securing privileged servers, control systems, databases, and network devices to keep your organisation safe from sophisticated cyber threats.
Explore diverse protection methods like the Principle of Least Privilege (PoLP), Multi-Factor Authentication (MFA), Secure Remote Access, and Encryption. Each module offers in-depth insights and practical experience in these techniques, ensuring your digital assets are safeguarded.
Tailored for IT professionals and cybersecurity enthusiasts, this course transforms your approach to cybersecurity. Gain vital skills and confidence to manage and implement effective security measures, making you a crucial player in protecting your organisation. Join us to become a cybersecurity champion and fortify your organisation’s defences.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
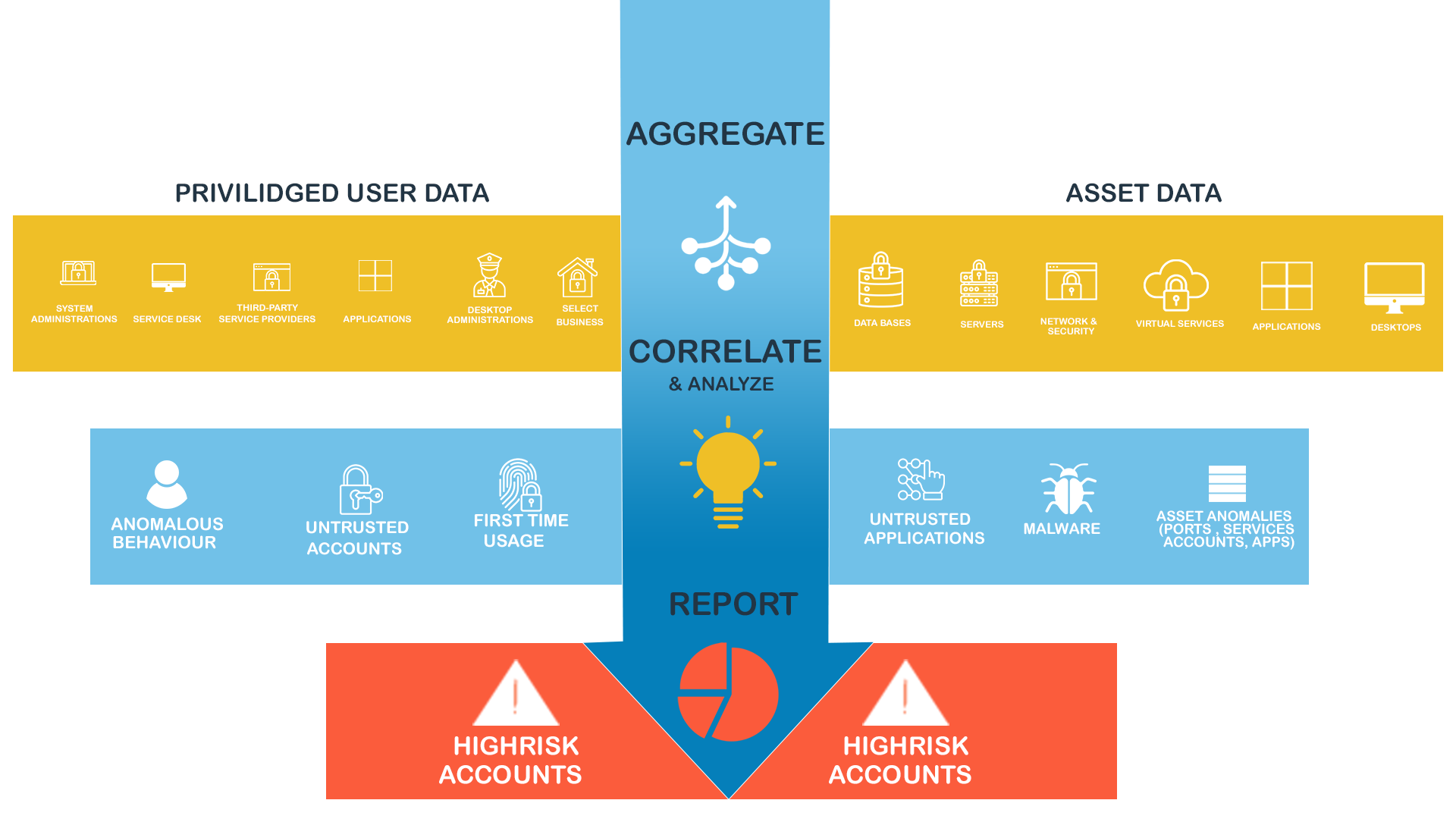
What is privileged access management?
The practice of controlling and monitoring the use of privileged access.
Privileged access management (PAM) is the practice of controlling and monitoring the use of privileged access (i.e., administrative or superuser access) within an organisation.
This typically involves the use of security measures and controls to ensure that only authorized users are granted access to privileged accounts and functions, and that the use of such privileges is monitored and audited.
Privileged access management is important because it helps to protect against unauthorised access to sensitive systems and data, and to ensure that only authorised users are able to perform certain actions that could have a significant impact on the organization.
Some common components of Privileged access management include privileged account password management, least privilege principles, access control, and auditing and reporting.