Master PAM Automation: A Comprehensive Course on Deploying, Optimizing, and Scaling Solutions in IT Ecosystems
This course delves deep into PAM automation, blending technical depth with strategic insight and practical application. It's designed for those aiming to enhance their organization's cybersecurity by managing privileged access more effectively.
Learn the intricacies of PAM deployment models to align with your organizational goals and IT infrastructure. Our curriculum focuses on performance optimization to ensure your PAM solutions are secure yet efficient, minimising impact on system resources and user productivity.
We address scalability challenges, preparing you to manage system and user base growth without compromising security. The course also develops your skills in creating effective Request for Information (RFI) documents for PAM vendors, enhancing your ability to make informed decisions.
Ideal for IT professionals, system administrators, and business leaders, this course provides the knowledge to integrate advanced PAM strategies into your cybersecurity framework, positioning you as a key player in combating cyber threats. Join us to transform your approach to privileged access management and secure your organization's digital future.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
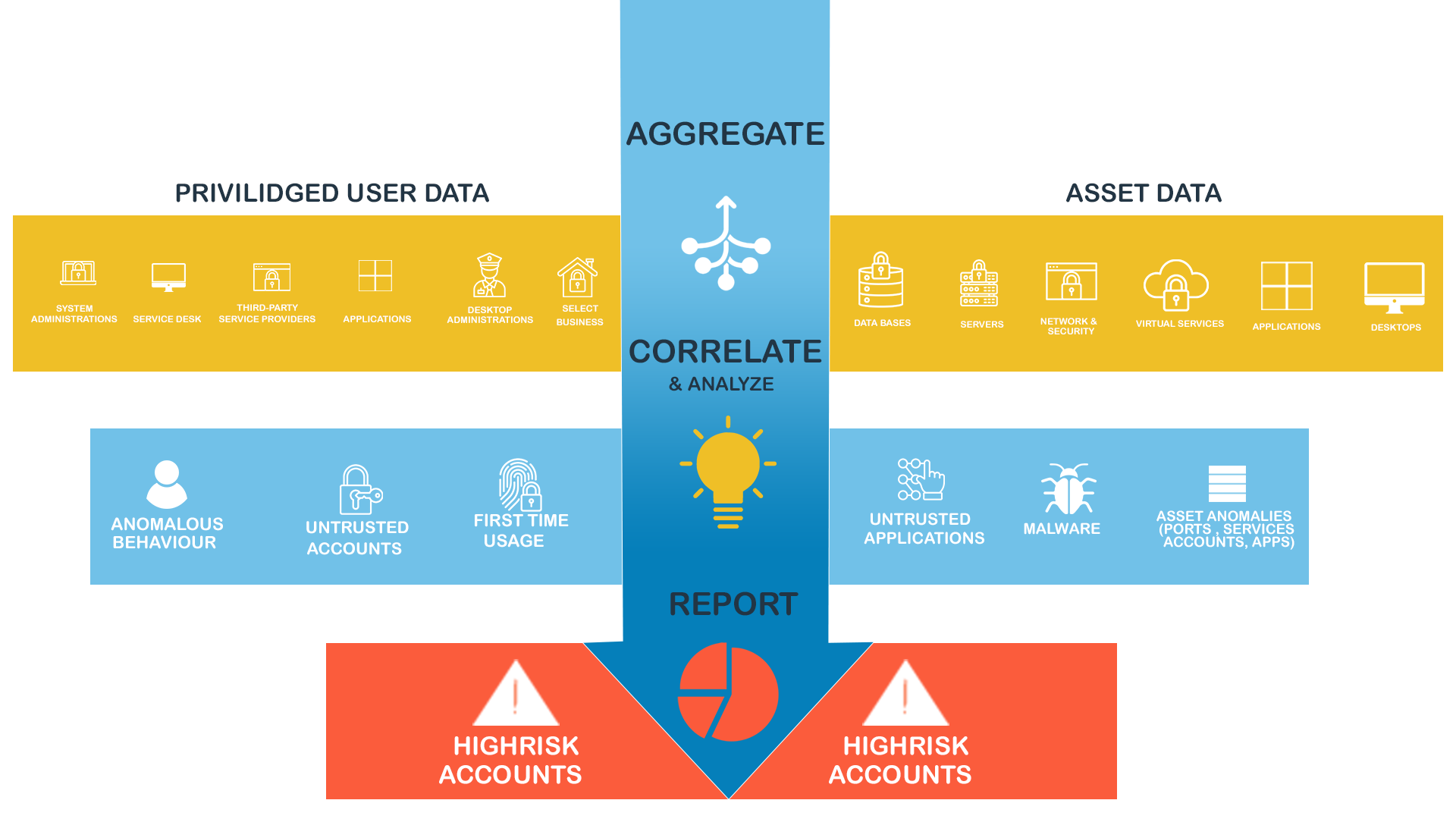
What is privileged access management?
The practice of controlling and monitoring the use of privileged access.
Privileged access management (PAM) is the practice of controlling and monitoring the use of privileged access (i.e., administrative or superuser access) within an organisation.
This typically involves the use of security measures and controls to ensure that only authorized users are granted access to privileged accounts and functions, and that the use of such privileges is monitored and audited.
Privileged access management is important because it helps to protect against unauthorised access to sensitive systems and data, and to ensure that only authorised users are able to perform certain actions that could have a significant impact on the organization.
Some common components of Privileged access management include privileged account password management, least privilege principles, access control, and auditing and reporting.