
Why Privileged Access Management (PAM) Training Matters
Elevating Security Through Human-Centric, Business-Aware PAM Education
In today’s threat landscape, securing privileged access is not just a technical task — it’s a business-critical function.
Yet, across the cybersecurity industry, we see a consistent pattern: training is focused heavily on tools and vendors, while neglecting the wider picture — business processes, human behaviour, and the real-world operational impact of privileged access.
At PAM Best Practice, we believe this is a dangerous gap — and we're here to fill it.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
The Problem with Current Training Models
Too often, PAM training looks like this:
Too often, PAM training looks like this:
-
Product certification courses with narrow use-case demos.
-
Deep technical dive-ins that assume business alignment happens elsewhere.
-
Minimal attention to how privileged access ties into governance, risk, compliance, or human workflows.
This results in professionals who are technically capable — but unable to design or defend PAM strategies that support business resilience, regulatory compliance, or sustainable user adoption.
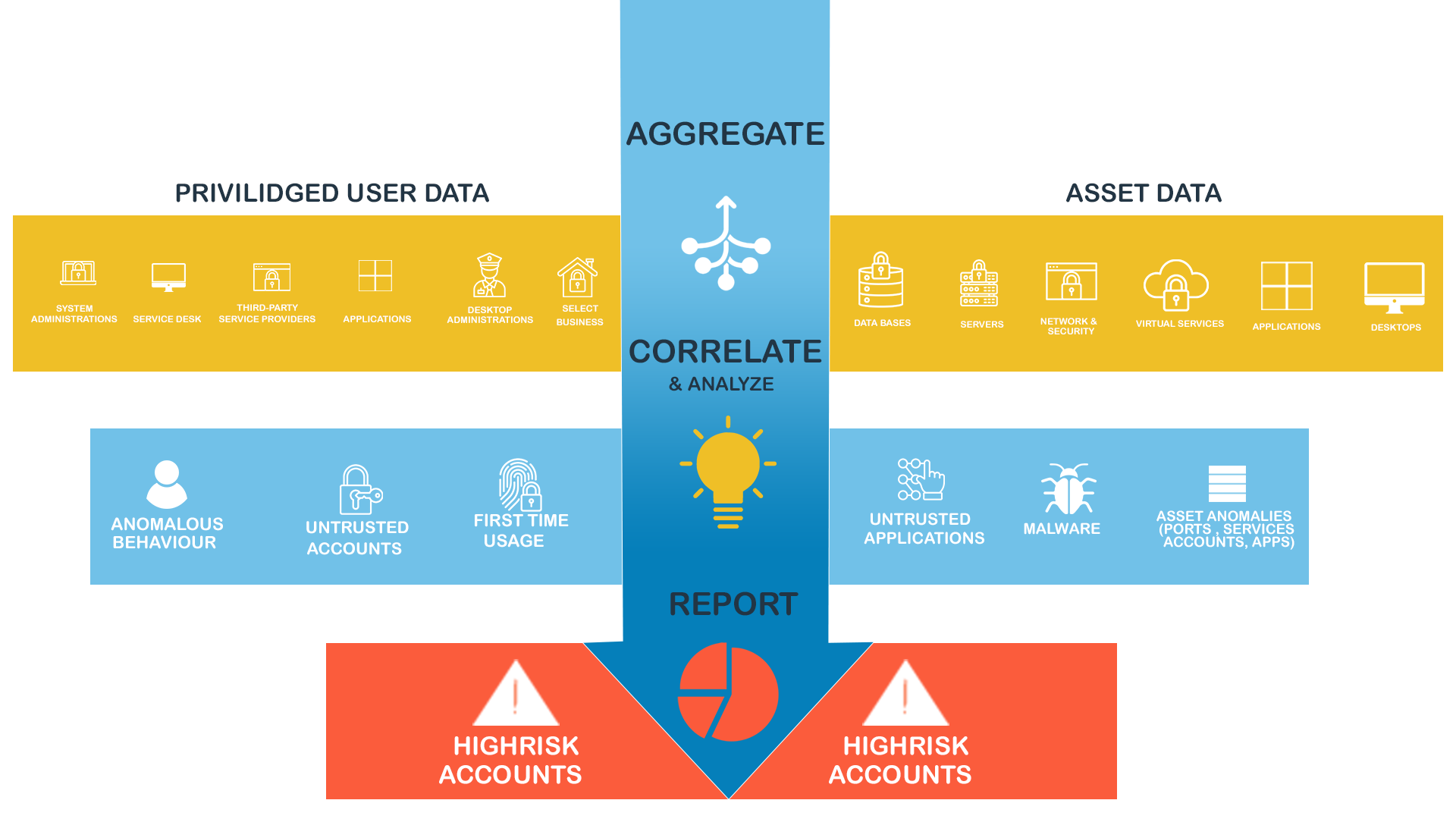

Our Vision: Experience-Led, Holistic PAM Training
We’re building a community for PAM professionals, by PAM professionals — with real-world experience at its core.
Our training isn’t just about “how to configure a vault” or “which API to use.” We focus on:
✅ Business Process Alignment – Embedding PAM in operations without friction
✅ Human Factors – Understanding how people interact with privilege
✅ Design Thinking – Building secure, scalable, and user-friendly PAM solutions
✅ Real-World Scenarios – Lessons learned from enterprise deployments and breaches
✅ Cross-Industry Insight – Best practices from finance, healthcare, education & more
The PAM Periodic Table: A Blueprint for Success
At the heart of our course is our PAM Periodic Table — a structured framework we’ve developed that outlines all the essential elements needed for a successful PAM program.
Time and time again, we see PAM projects fail not due to technical issues, but because they overlook critical elements like process ownership, stakeholder engagement, change management, or integration planning.
Our Periodic Table helps prevent that — providing a clear, repeatable model to design, assess, and mature any PAM deployment.
Help Us Build the Next Generation of PAM Defenders
We’ve already produced a number of educational videos based on our scripts and frameworks, but we’re not stopping there. We’re engineers with full-time roles who are deeply passionate about raising the bar in the PAM space — but to do this right, we need your help.
We’re currently seeking sponsors to help us:
🎥 Professionally produce high-quality training videos
📘 Publish course materials based on our PAM Periodic Table
🎙️ Launch community-led workshops, webinars, and events
🌍 Expand access to knowledge for new and aspiring PAM practitioners
If you're an organisation that cares about cybersecurity maturity, or a vendor that believes in long-term customer success through education, we’d love to hear from you.
Join the Movement
Whether you're a seasoned practitioner or just stepping into the PAM world, we invite you to be part of a growing network of professionals committed to shaping the future of access security.
At PAM Best Practice, we're not just offering training — we're building a platform for progress.
