What is privileged access?
Privileged access refers to the level of access or permissions granted to a user or entity within a system or organisation.
This level of access is typically reserved for individuals or entities who require access to sensitive data or systems, such as network administrators or IT staff.
Privileged access often includes the ability to perform administrative tasks, make changes to system configurations, and access confidential information.
If an unauthorized user gains privileged access, they may be able to exploit vulnerabilities, steal sensitive data, or cause significant damage to systems and infrastructure. As a result, it is important for organisations to carefully manage and monitor privileged access to reduce the risk of security breaches.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
The collapse of Barings Bank in 1995.
The collapse of Barings Bank serves as a cautionary tale about the importance of robust IT systems and proper oversight and controls. The failure of the bank's IT systems made it easier for a rogue trader to cover up losses and ultimately led to the bank's demise.
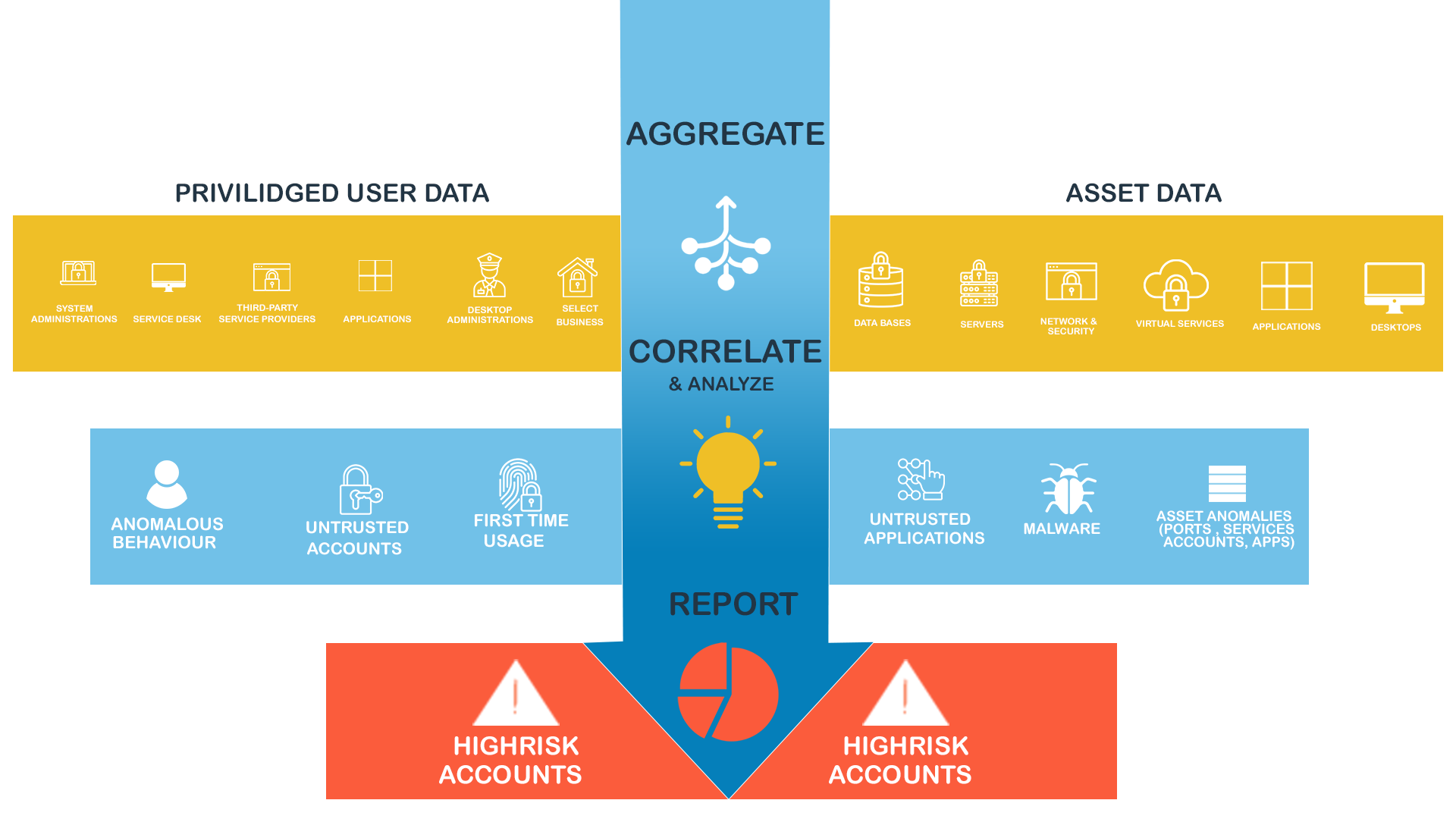
What is privileged access management?
The practice of controlling and monitoring the use of privileged access.
Privileged access management (PAM) is the practice of controlling and monitoring the use of privileged access (i.e., administrative or superuser access) within an organisation.
This typically involves the use of security measures and controls to ensure that only authorized users are granted access to privileged accounts and functions, and that the use of such privileges is monitored and audited.
Privileged access management is important because it helps to protect against unauthorised access to sensitive systems and data, and to ensure that only authorised users are able to perform certain actions that could have a significant impact on the organization.
Some common components of Privileged access management include privileged account password management, least privilege principles, access control, and auditing and reporting.