Navigate Compliance and Merge AI with PAM: Master the Convergence of IAM and PAM Protocols in Our Comprehensive Course.
This curriculum demystifies PAM integration in the cloud era, exploring how automation and cloud technologies enhance cybersecurity foundations. You'll learn to use these advancements to better protect your organization's digital assets and delve into Zero Trust architecture, which transforms security strategies by ensuring trust is continually verified.
Discover how AI can improve PAM operations, making security more predictive and proactive. Understand the vital role of compliance in shaping security frameworks and gaining a strategic advantage by staying ahead of regulatory changes.
The course goes beyond current trends, preparing you for future cybersecurity challenges. Ideal for IT professionals, cybersecurity strategists, and business leaders, it provides essential insights and skills to navigate complex PAM scenarios.
Embark on this transformative journey in Privileged Access Management and become a leader in driving cybersecurity innovation within your organization. Don't miss this opportunity to lead in the evolving field of cybersecurity.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
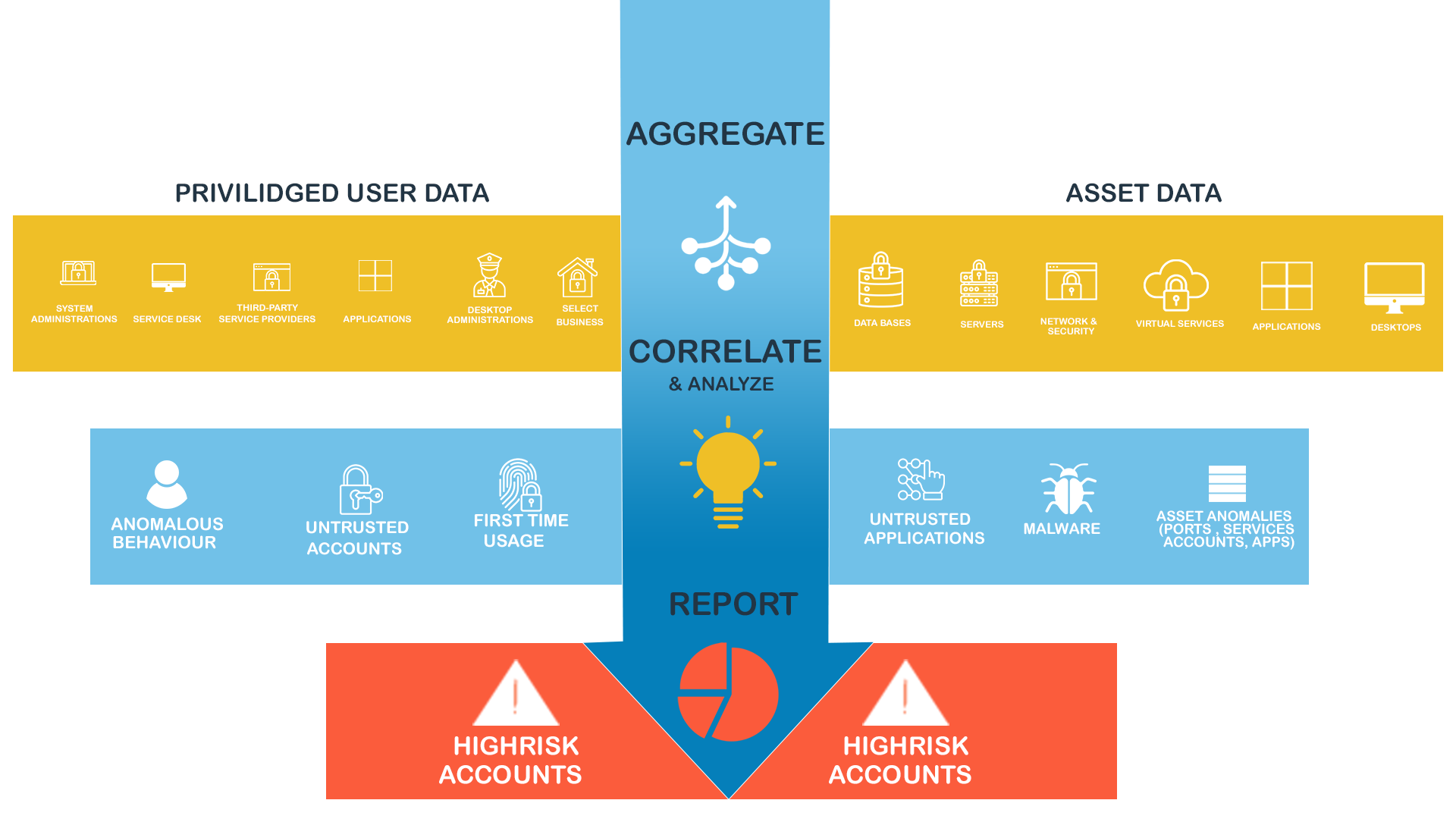
What is privileged access management?
The practice of controlling and monitoring the use of privileged access.
Privileged access management (PAM) is the practice of controlling and monitoring the use of privileged access (i.e., administrative or superuser access) within an organisation.
This typically involves the use of security measures and controls to ensure that only authorized users are granted access to privileged accounts and functions, and that the use of such privileges is monitored and audited.
Privileged access management is important because it helps to protect against unauthorised access to sensitive systems and data, and to ensure that only authorised users are able to perform certain actions that could have a significant impact on the organization.
Some common components of Privileged access management include privileged account password management, least privilege principles, access control, and auditing and reporting.