Unlock the Secrets of Cybersecurity: Master Privileged Access Management with Our Latest Industry-Relevant Curriculum
By the end of this course, you will have a comprehensive understanding of Privileged Access Management, enabling you to make informed decisions, implement best practices, and contribute to a more secure digital environment.
Get ready to embark on a journey towards PAM mastery and become a guardian of privileged access in today's cybersecurity landscape. Let's get started!
Explore 9 Comprehensive Modules: Industry-Based Curriculum in Privileged Access Management.
Module 1: Foundational Pillars of PAM
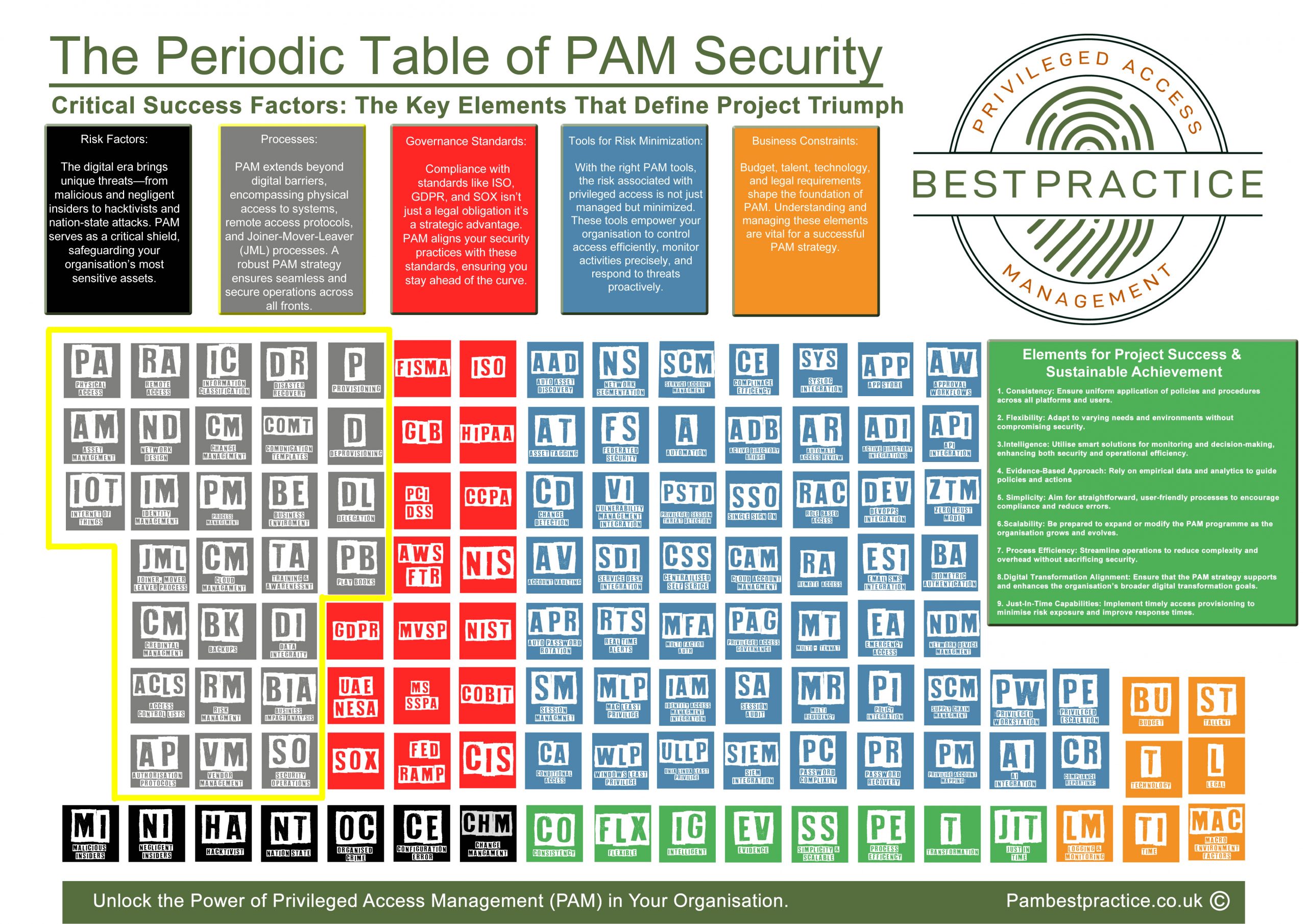
Introduction to PAM: Unveil the essence of PAM and discover why it is crucial in the realm of cybersecurity.
Discover PAM's crucial role in cybersecurity, explore its varied access types, and real-world applications. Learn and apply holistic PAM blending theory with practical insights for mastery.
Module 1, Part 2: Threat Landscape & PAM
Introduction to PAM part 2: Examine the evolving PAM threat landscape. Learn to effectively mitigate risks from negligent insiders, hacktivists, nation-states, organized crime, and the challenges of configuration errors and poor change management for robust cybersecurity.
Module 2, Part 2: Initiating PAM Implementation
Understand the critical importance of stakeholder engagement, change management, and strategic communication. Thoroughly examine key business processes such as provisioning, deprovisioning, delegation, and joiner-mover-leaver processes for effective PAM.
Module 3, Part 1: Discovery & Assessment in PAM
Embrace the crucial discovery and assessment phase: Extract deep insights from access control lists, conduct role-based analysis reviews, scrutinize privileged user lists, perform thorough active directory reviews, and leverage IAM tools for enhanced PAM.