Master Cybersecurity Fundamentals: Unlock the Discovery and Assessment Phase with Our Comprehensive PAM Course.
Embark on a transformative journey into Privileged Access Management (PAM) with our specialized course, guiding you through the crucial discovery and assessment phase of PAM implementation. This course highlights the complexities of cybersecurity, focusing on effectively mapping and understanding privileged access within an organization.
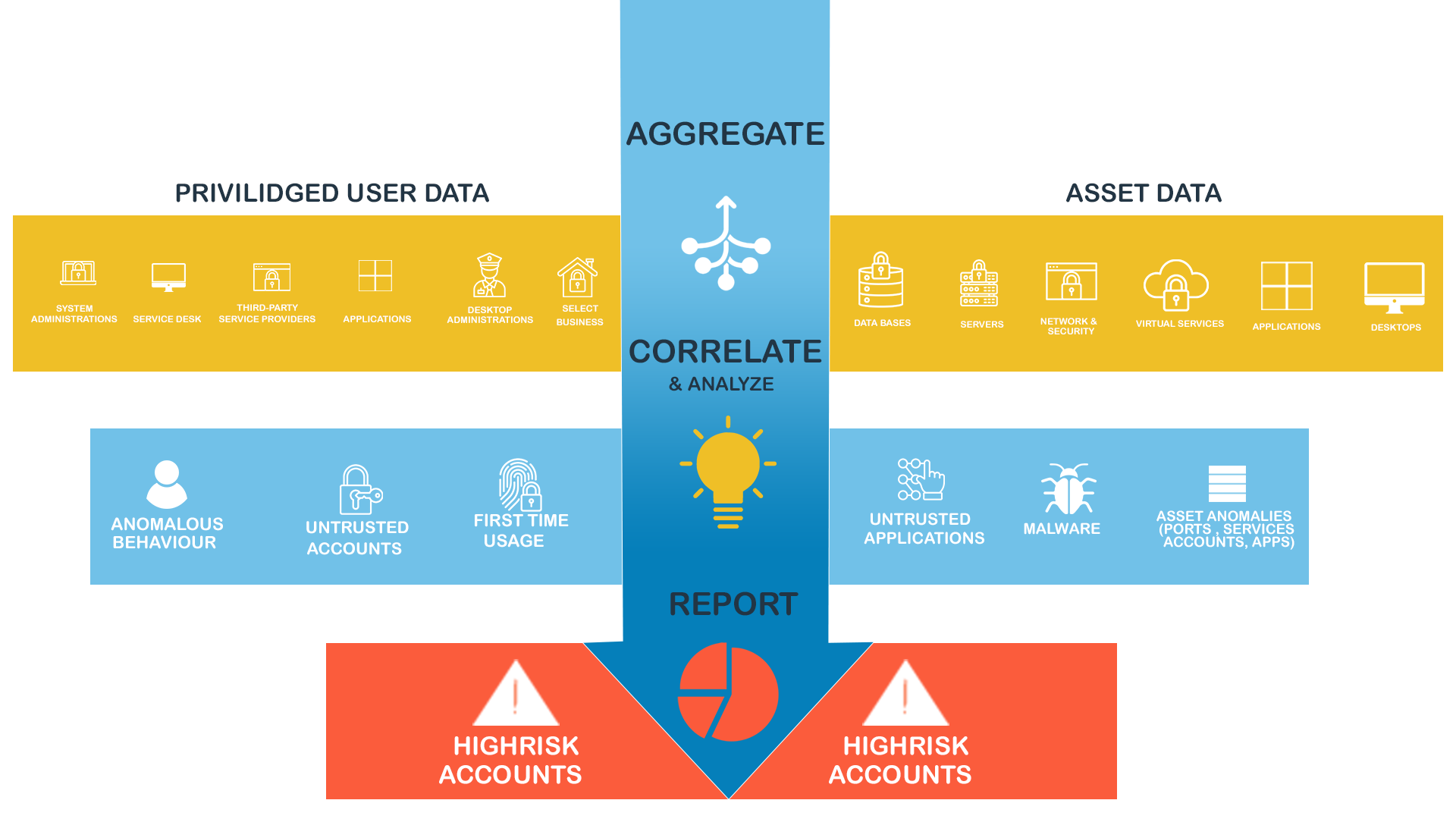
Our curriculum meticulously covers the "Discovery and Assessment Phase," teaching you to identify and catalogue privileged accounts, roles, and access permissions—essential for crafting a robust PAM strategy. You'll use advanced tools and methodologies to analyze access control lists, perform role-based reviews, and employ cutting-edge Identity and Access Management (IAM) tools.
This phase is more than procedural; it’s a strategic exploration of the methods underpinning successful PAM operations. With detailed evaluations, you’ll identify vulnerabilities, apply the principle of least privilege, and lay the groundwork for a solid PAM framework.
Ideal for aspiring cybersecurity experts, IT managers, or business executives, our course delivers the insights and practical knowledge needed to advance your career and secure your organization's critical digital assets. Join us to enhance your strategic decision-making and fortify your organization against cyber threats.
Types of privileged accounts within a typical organisation:
Root Accounts
Administrator Accounts
Cloud Infrastructure Accounts
Shared Accounts
SSH Keys
Hard Coded Accounts
Backup Accounts
Local Accounts
Service Accounts
Network Device Accounts
Named Privileged Accounts
What is privileged access management?
The practice of controlling and monitoring the use of privileged access.
Privileged access management (PAM) is the practice of controlling and monitoring the use of privileged access (i.e., administrative or superuser access) within an organisation.
This typically involves the use of security measures and controls to ensure that only authorized users are granted access to privileged accounts and functions, and that the use of such privileges is monitored and audited.
Privileged access management is important because it helps to protect against unauthorised access to sensitive systems and data, and to ensure that only authorised users are able to perform certain actions that could have a significant impact on the organization.
Some common components of Privileged access management include privileged account password management, least privilege principles, access control, and auditing and reporting.